The Booz Allen DarkLabs’ Threat Hunt team recently discovered a unique form of adware lurking on networks that evades all traditional forms of cyber defenses. The adware is a previously known threat that is commonly used to inject advertisements into a user’s browser and covertly collect information about the user’s browsing activity.
Adware is often ignored during security operations because it is generally considered unsophisticated, is prevalent, and has a low perceived threat level. This adware, which we are calling advanced persistent adware (APA), is unique because it leverages advanced techniques, typically only seen in attacks attributed to nation-state-level advanced persistent threats (APT), to evade detection, maintain persistence, and connect to a command and control (C2) server to facilitate the second stage of the attack. This APA is similar to adware detected by Carbon Black’s Endpoint Detection and Response (EDR) platform. Both examples demonstrate the growing need for advanced detection as the playing field continues to evolve in favor of these threats.
The APA has been classified as an Advanced JavaScript-Based In-Memory Stage 1 Downloader because it is built on JavaScript, runs strictly in memory, and functions as the downloader for the second stage of the APA’s attack. It is delivered as a Trojan via a third-party installer on the internet and avoids anti-virus detection by leveraging many polymorphic techniques, such as randomizing its file name, file path, and payload. While stored on disk, the payload is comprised of hex-encoded JavaScript surrounded by thousands of bytes of junk hexadecimal characters that serve to obscure the true intent of the file and avoid anti-virus detection when scanned.

 Example of Payload
Example of Payload
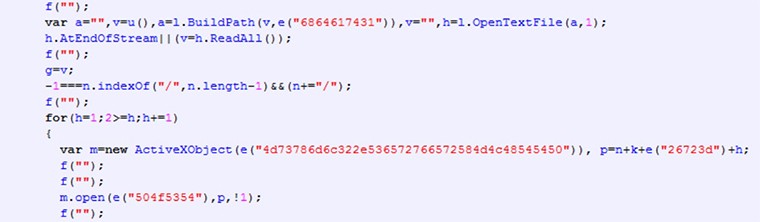 Sample of Decoded JavaScript
Sample of Decoded JavaScript

